Employ AI to accelerate your switch from your current SIEM to Elastic Security
Adopt Elastic Security faster — without manually rebuilding SIEM content — using Automatic Migration, powered by Search AI

Migrating detection rules, dashboards, and other artifacts is one of the most challenging aspects of switching SIEMs. Generative AI can ease this burden.
Automatic Migration, new in Elastic Security 8.18 and 9.0, maps and translates existing detection rules, thereby lowering the effort and complexity of transitioning to a new SIEM. It complements Automatic Import, which creates custom data integrations, and other AI-based capabilities from Elastic. We’re starting with Automatic Migration for Splunk, with plans for additional SIEMs soon. Support for additional SIEM artifacts, like dashboards and visualizations, is also on the way.
Automatic Migration reliably transfers even complex Splunk detection rules to Elastic Security. The feature maps existing rules to Elastic-built rules using semantic search powered by the ELSER natural language processing (NLP) model, which matches equivalent rules even without exact text matches. It translates any rules that are not mapped — including associated lookups and macros — into new Elastic queries using generative AI grounded in custom knowledge. Automatic Migration then validates translated rules and provides an intuitive interface for quick installation.
Elastic engineers have validated Automatic Migration by evaluating its performance with real-world rulesets and conducting extensive error testing. We've also tested it across a range of AI models — results you can view in Elastic Security’s LLM performance matrix.
Automatic Migration is offered in technical preview to all customers with an Enterprise license or the Security Analytics Complete tier of Elastic Cloud Serverless.
Automatic Migration in action
Let’s see how this capability works.
Automatic Migration is available from Elastic Security’s “Get started” page. It runs on demand, enabling customers to migrate rules at their own pace and supporting the consolidation of multiple Splunk deployments.
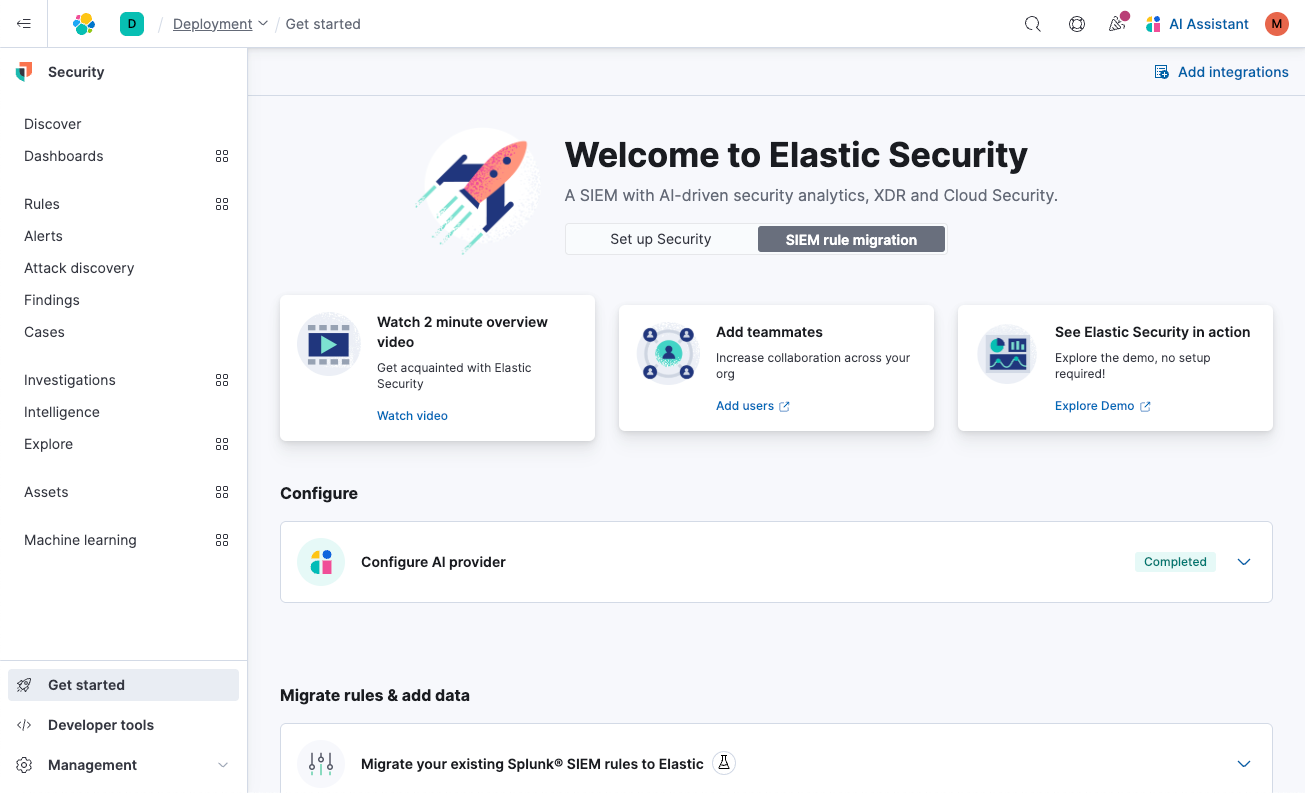
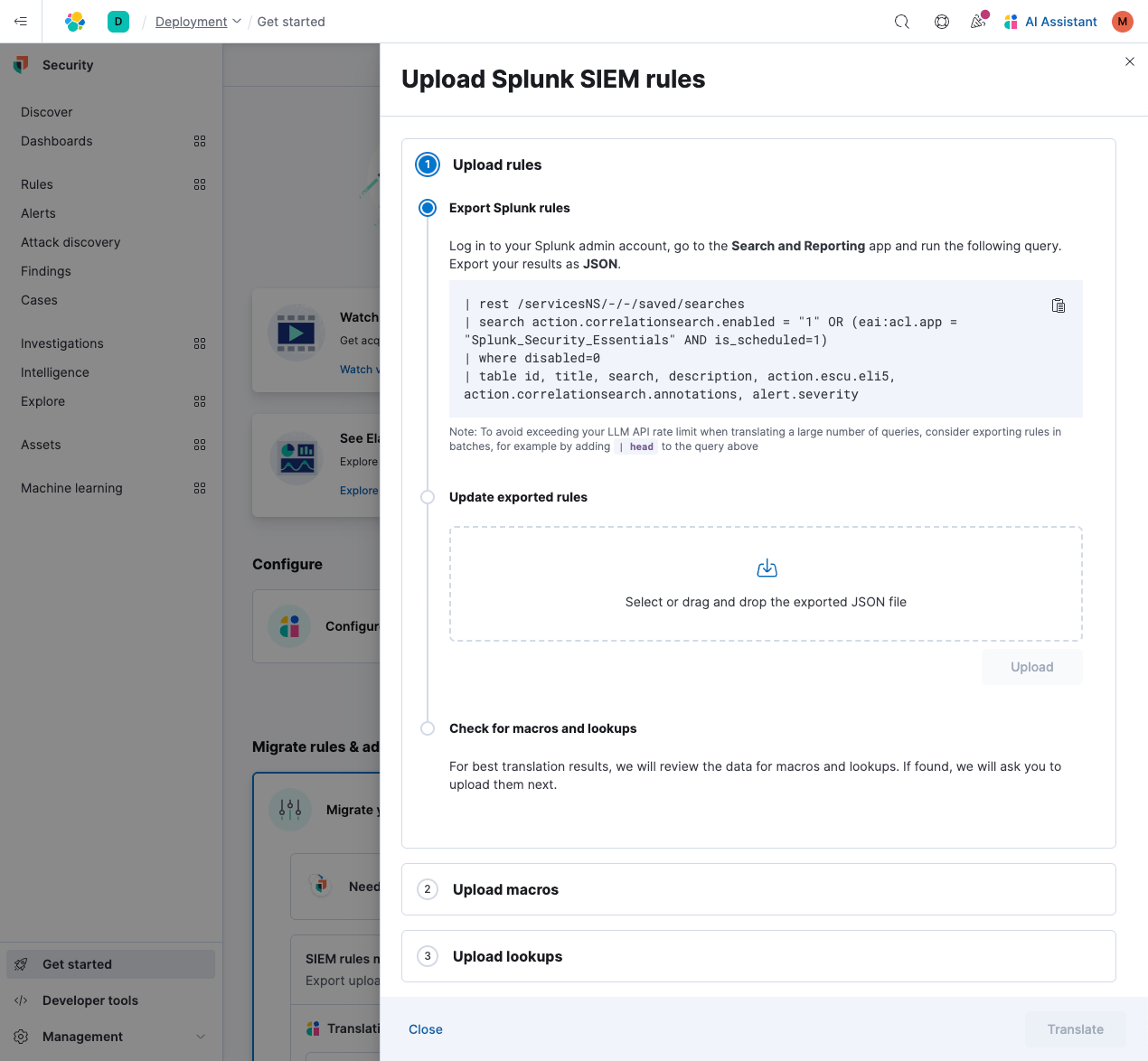
The feature guides users to export their detection rules from Splunk and upload them. It scans for references to macros and lookups and, when found, prompts you to upload them, too. The system incorporates this logic to maintain functional equivalence with the original detection.
Map your existing rules to prebuilt rules using semantic search
Automatic Migration maps many existing rules to the 1,300+ detection rules provided by Elastic Security Labs, covering use cases across the MITRE ATT&CK matrix. Utilizing semantic search powered by ELSER, it deciphers the title, description, and query of each rule to identify equivalents based on intent, rather than relying solely on exact text matches. These rules are actively maintained by Elastic’s engineers, minimizing customer upkeep. While mapping existing rules manually requires significant time and domain expertise, Automatic Migration typically completes the process in just minutes.
Translate existing rules into new rules using AI grounded in custom knowledge
When corresponding prebuilt rules aren’t available, Automatic Migration creates custom rules and validates them to ensure functionality. It begins by identifying prebuilt data integrations relevant to the query using retrieval augmented generation (RAG). The feature then translates the query from Search Processing Language (SPL) into ES|QL, leveraging AI grounded in custom knowledge. It then deterministically validates its syntax — looping, if necessary, to revise and retest its logic. This process ensures that each fully translated rule adheres to Elastic’s schema and structure, enabling reliable rule execution and performance.
A closer look at rule mapping and translation
This flowchart illustrates how Automatic Migration functions:
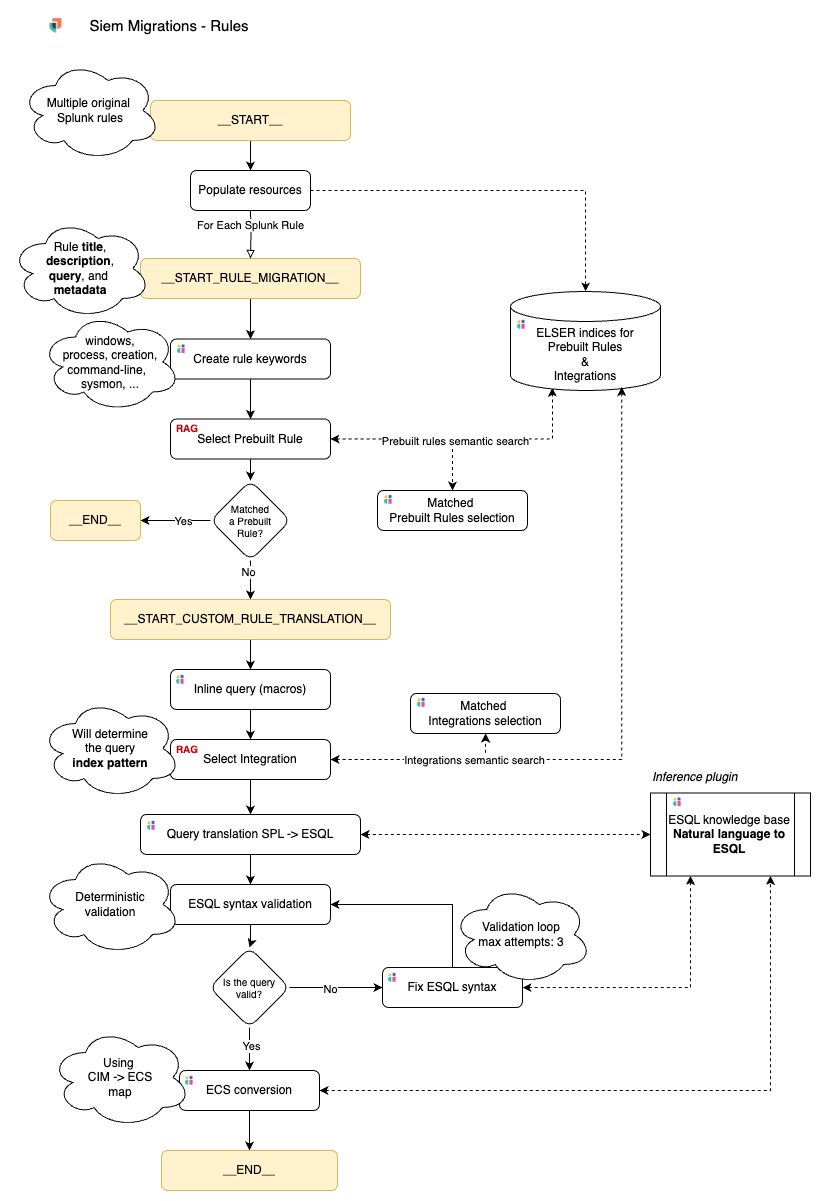
Let’s break down the steps highlighted above.
The user uploads the Splunk rules, macros, and lookups exported via the provided SPL query, which can be modified — for example, to filter rules by app or age.
Automatic Migration attempts to map the Splunk rules to Elastic’s prebuilt rules. In the background, it generates vectorized representations (embeddings) of Elastic’s prebuilt detection rules using ELSER.
The feature uses a large language model (LLM) to generate keywords relevant to the content of each Splunk rule.
Automatic Migration runs semantic searches using the keywords from each Splunk rule against the embeddings of Elastic’s prebuilt rules, identifying potential matches.
Automatic Migration passes the semantic search results to the LLM, and a determination is made to see if it is an identical or very close match.
If a match is found, the prebuilt rule is added to the set of translated rules.
If no match is found, Automatic Migration proceeds to translate the SPL rule.
The LLM substitutes macros in the SPL query with their expanded form. If the query references lookups, the lookup file is indexed as a lookup index in Elasticsearch.
Once the LLM returns the SPL query with macros substituted, Automatic Migration performs another semantic query to identify any prebuilt integrations for data sources that may be needed to run the query.
Automatic Migration then translates the SPL query into ES|QL using an inference plugin designed to generate ES|QL queries from natural language requests — the same plugin used by Elastic AI Assistant. It contains a catalog of all available ES|QL functions and how they can be used. Instructions relevant to the original query are leveraged by the LLM.
Automatic Migration validates the syntax of the translated query. If it is not valid, the query — along with the returned error code — is sent back to the LLM for correction. This loop runs up to three times.
If the query is valid, Automatic Migration directs the LLM to map specific fields from the Splunk Common Information Model (CIM) to Elastic Common Schema (ECS). If no direct mapping is found and the LLM cannot determine an appropriate ECS field, the field names are left as is.
Review and install your translated rules
Automatic Migration displays all translated rules and provides direct access to each one. The rules are sorted by translation status:
Mapped or custom rules that are fully translated and ready to install
Partially translated rules that require user action
Rules that could not be translated, likely due to functional differences between the query languages
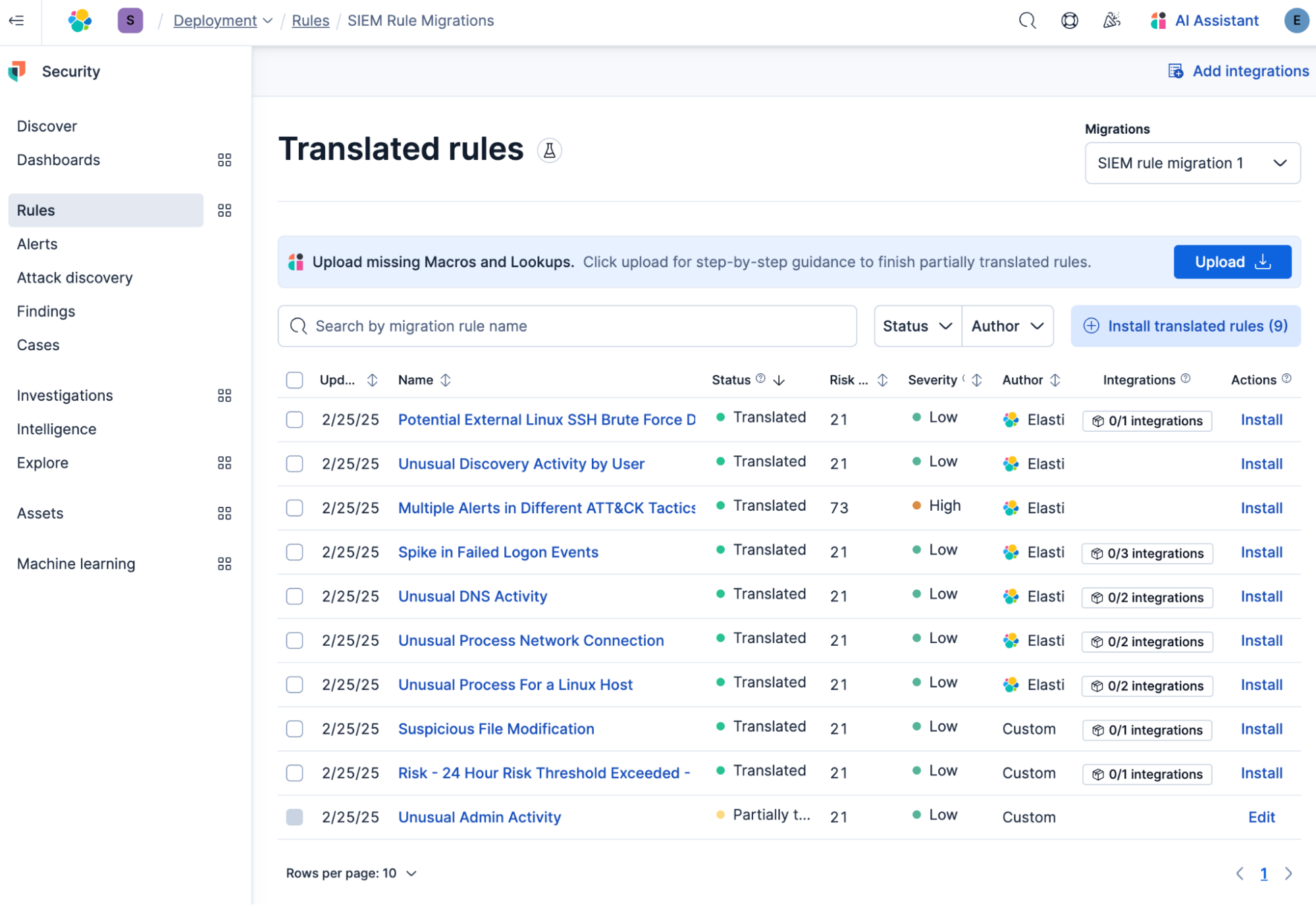
You can examine individual rules with one click. The Translation tab presents the source and Elastic versions side-by-side to enable efficient comparison. You can make edits and get contextual help from Elastic AI Assistant on matters like rule syntax and logic. From the Overview tab, you can view details like the rule's severity, risk score, and execution interval.
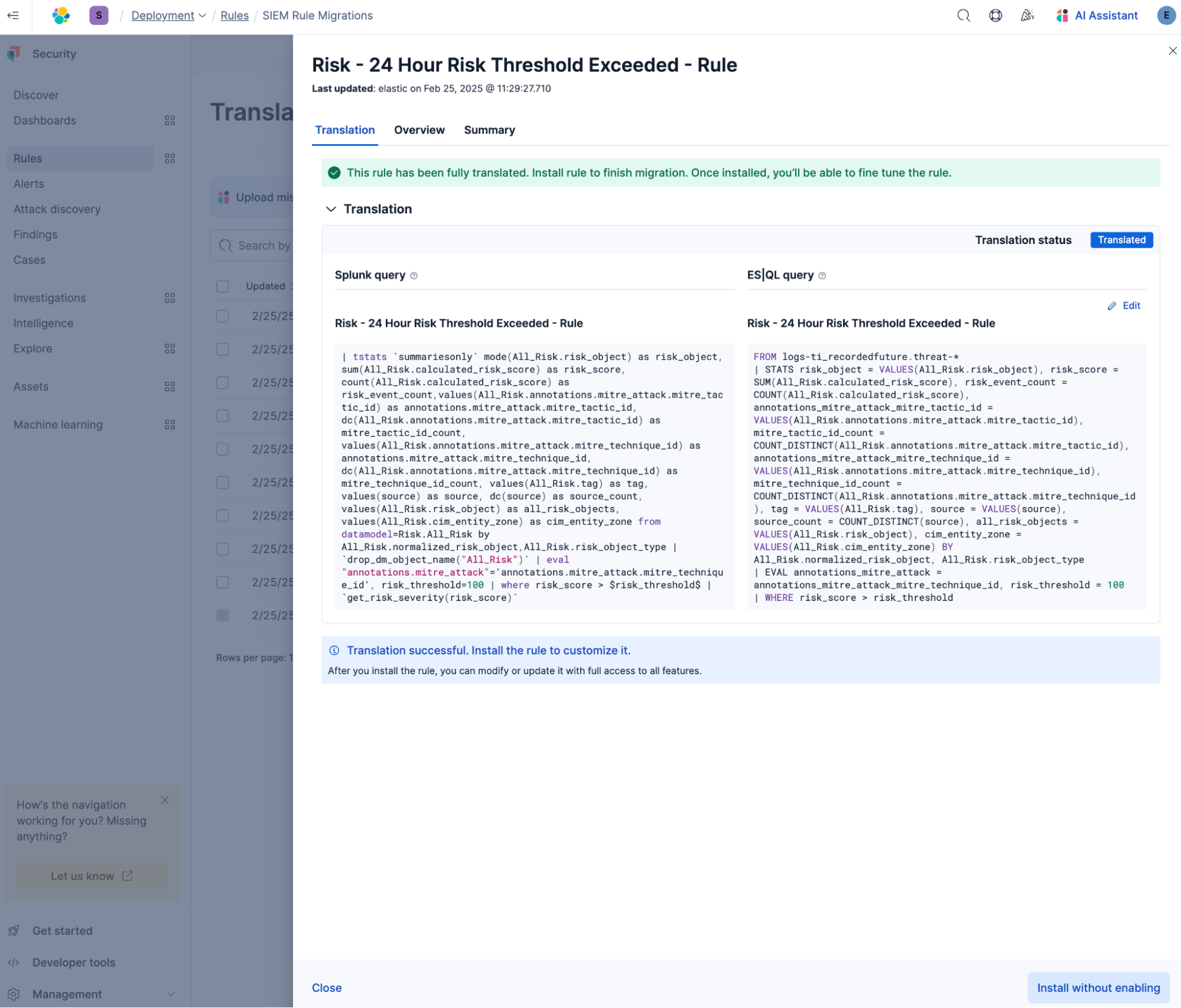
See for yourself with AI that shows its work
Understanding and trusting your detections is critical, so Automatic Migration explains in detail how each rule was mapped or translated. The Summary tab outlines the rationale behind key decisions — such as field assignments and the use of specific ES|QL commands — and highlights any missing macros or lookups. This transparency helps you validate the translated rule's behavior and ensure alignment with your detection goals.
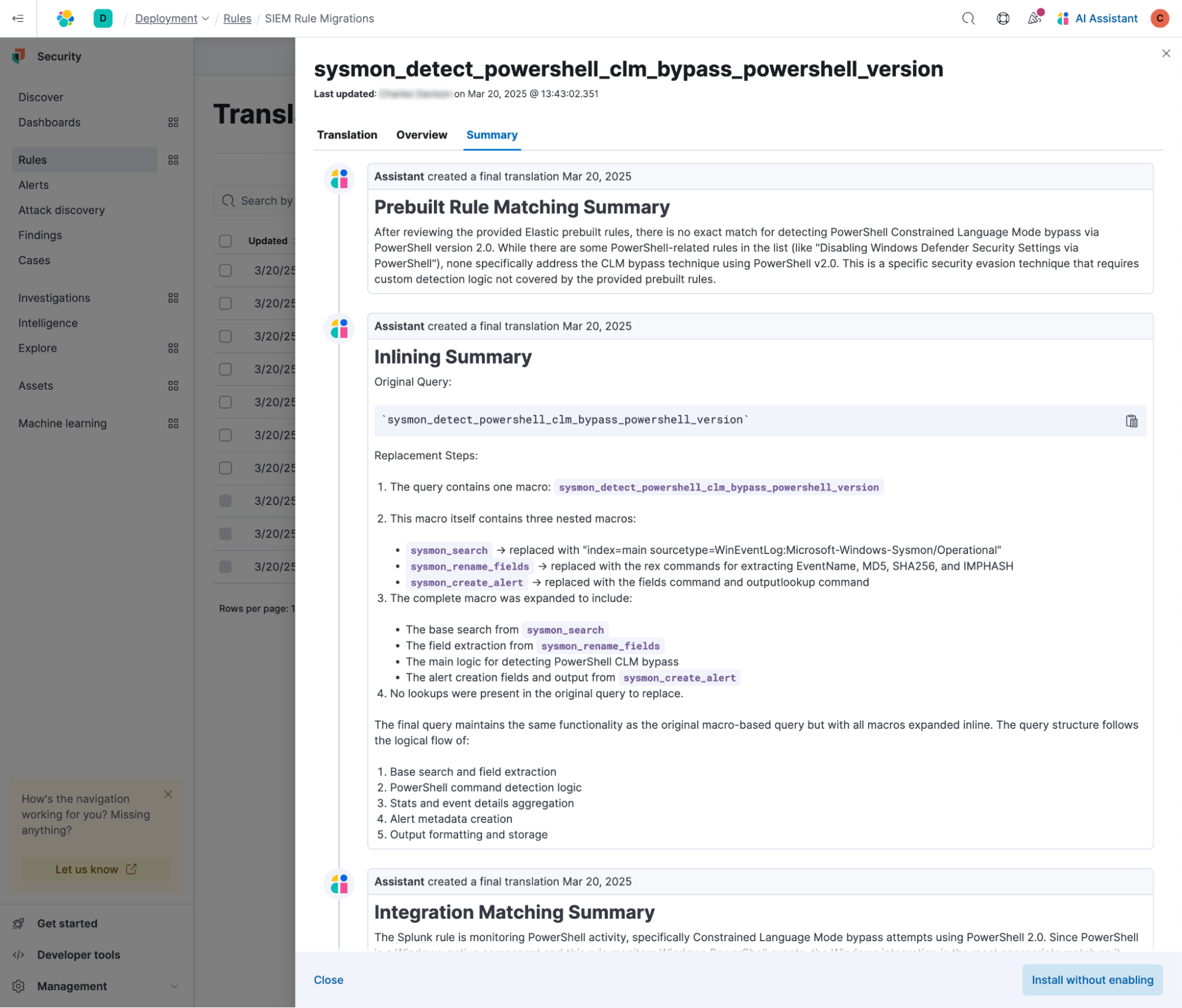
When a rule is only partially translated, Automatic Migration identifies blockers, such as misaligned index names or missing columns. You can upload any missing macros or lookups with step-by-step guidance, and if required data isn’t available, the feature suggests relevant integrations.
Once ready, you can install fully translated rules with one click.
How Elastic’s AI features aid SOC teams
Elastic Security’s AI features help SOC teams strengthen defenses across the IT environment:
Automatic Migration complements Elastic’s deep library of prebuilt rules to broaden detection use case coverage.
Automatic Import extends visibility — and powers detection rules — by onboarding custom data sources in minutes.
Attack Discovery distills the alerts generated by detection rules to pinpoint advancing threats and suggest next steps.
- Elastic AI Assistant guides analysts through investigation and response using natural language.
Explore switching to Elastic Security
We’re excited for you to begin using Automatic Migration. Have feedback? Tell us what you think in Elastic’s community Slack channel or on the Elastic Security forum.
Interested in using Elastic Security in your SOC? Try it free or get in touch.
Splunk and other related marks are trademarks or registered trademarks of Splunk Inc. in the United States and other countries. All other brand names, product names, logos, or trademarks belong to their respective owners.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third-party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos or registered trademarks of Elasticsearch B.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.