

What is SIEM (security information and event management)?
SIEM (security information and event management) definition
Security information and event management (SIEM) solutions collect logs and events for security teams to analyze as visualizations, alerts, searches, reports, and more. This information can help security teams detect threats in real time, manage incident response, perform forensic investigation on past security incidents, and prepare audits for compliance purposes.
To detect threats and other anomalies, a SIEM ingests and analyzes a high volume of data in seconds to find and alert on unusual behavior. Monitoring data from all sources in real time — including network applications, hardware, cloud, and more — can help organizations stay ahead of internal and external threats.
Security teams will often use their SIEM as a central dashboard, conducting day-to-day operations within the solution. Security analysts can use SIEM solutions to take on advanced cybersecurity use cases such as continuous monitoring, threat hunting, and incident investigation and response.
How does SIEM work?
In order to monitor and analyze, a security information and event management system must pull data from all over the organization. Many SIEMs deploy agents — like Elastic Agent — on user devices, servers, network equipment, and more. Additionally, SIEMs often integrate with cloud service providers to watch over cloud-specific infrastructure.
All of this data will be stored — for example, in Elastic’s Search AI Lake — for security teams to conduct investigations on or to prove compliance to government agencies.
SIEM capabilities and features
There is quite a bit of functionality involved with a SIEM solution. Some of the major capabilities include:
- Advanced detection: Detection takes a lot of forms. Malware, like ransomware or viruses, as well as changes in credentials, insider threats, data exfiltration, and anomalous behavior are all items a SIEM should be able to identify.
- Alerting: As a SIEM is analyzing, it will inform security teams of immediate issues through email, messaging, or dashboards.
- Continuous monitoring: Actively monitoring one’s environment can help analysts detect anomalous trends that may indicate a threat. Monitoring across the environment can include searching for system changes, network flow, or uptime and downtime.
- Compliance: Compliance with applicable mandates and frameworks, like HIPAA or the GDPR, is important for SIEMs. Many SIEMs will also have reporting capabilities and reporting on them. Different compliance mandates will vary across industries and regions (e.g., HIPAA for healthcare, GDPR within the EU).
- Visualizations and reports: A SIEM system will generate visualizations for practitioners to review event data and patterns, and many will generate reports that can be shared with SOC leaders and CISOs.
- Incident response: If a security incident has occurred, a coordinated response is necessary to mitigate the breach’s impact.
- Log management: The log data and events created by an organization’s hosts, apps, and networks need to be collected, stored, and analyzed through a centralized log management platform.
- Threat hunting: Threat hunting involves querying across vast amounts of data to actively hunt for threats.
All of these capabilities can be enhanced with artificial intelligence (AI) features, like Elastic AI Assistant for Security or Elastic Attack Discovery. We’re seeing how AI is rapidly changing the cybersecurity landscape for both defenders and attackers. Fortunately, SIEM solutions with embedded AI capabilities can give defenders the upper hand in this dynamic threat environment.
Learn more about AI adoption in security: Top use cases and mistakes to avoid.
History of SIEM
SIEM systems have been around for 20+ years and have evolved substantially from their early days as a centralized database. The first iterations of SIEM — which spawned from combined security information management (SIM) and security event management (SEM) — had heavy limitations on scaling, primitive alerting functionality, and scant data correlation capabilities.
Readers can dive into the full history of SIEM with our blog, Tracing history: The generative AI revolution in SIEM.
Over the years, SIEM technology would advance significantly in these previously underperforming capabilities, while also adding the ability to perform historical lookback on archival data — a helpful function for analysts to gain context on a potential threat.
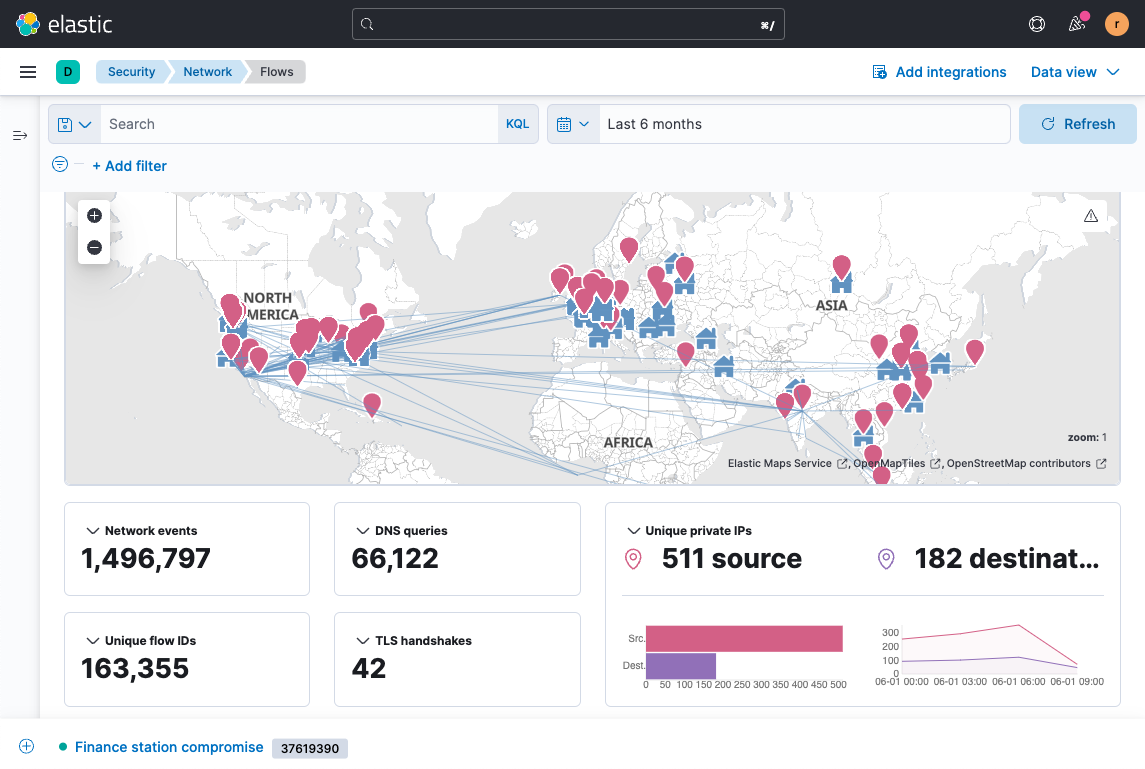
Now, visualization and integrated workflows are integral components of SIEM, orienting analysts to priority alerts and facilitating appropriate response actions. Modern SIEMs typically have detection and response workflows to help a security team more efficiently respond.
How does SIEM work?
A SIEM (security information and event management) platform works by collecting log and event data produced by these various technologies. It provides security analysts with a comprehensive view of their organization’s IT environment. An effective SIEM will automatically remediate known threats within a system, while surfacing more nuanced situations to help security analysts identify whether further investigation and action is needed.
Devices, networks, servers, apps, systems … an organization’s ecosystem produces a lot of data from daily operations. There’s an abundance of context within this data that can be helpful for keeping the ecosystem secure. That’s where SIEM comes in.
Why is SIEM important?
For many security teams, a SIEM is the primary component of their security operations center (SOC). It functions as a centralized hub through which massive amounts of data can be brought together for analysis, unifying the analyst experience by serving as the centralized mission-control base. With SIEM, a security team can identify and defend against threats that may have evaded perimeter security technologies and are active within the organization's ecosystem.
SIEM benefits
With a next-gen SIEM that can perform at speed and scale (many legacy SIEM solutions have limitations that prevent this), organizations are provided the following benefits:
- Holistic visibility: Having a single, centralized location from which teams can monitor, continuously analyze, and act within their environment is crucial in giving the security team a single source of truth.
- Unified narrative: A properly configured SIEM normalizes disparate data types to provide a cohesive snapshot of an organization's vast IT environment.
- Automated threat detection: Security practitioners can automate the detection of threats and anomalies and then quickly query data to investigate a series of events, access historical data for trends or context, and much more.
- Risk management: Through using a SIEM, teams can expose unknown threats with anomaly detection powered by prebuilt machine learning jobs — gaining insight into the entities at highest risk.
Deep dive into 9 benefits of AI-driven SIEM for boosting security
What's the difference between SIEM and SOAR?
While a SIEM solution provides security teams with a dashboard for visualizations, alerts, and reports to better detect threats, a SOAR (security orchestration, automation, and response) solution enables teams to standardize and streamline their organization's response to any detected incidents.
So, while SIEM specializes in detection of threats, SOAR specializes in the organization's broader response to those threats. In practice, the solutions are merging ever closer.
What is the future of SIEM?
To truly serve as the "single pane of glass" from which security practitioners can integrate with other technologies, SIEM (security information and event management) will need to evolve from its traditionally closed-off, "black box" approach. This means security software developed out in the open, where anyone can see what features are working to keep users secure and what code can be enhanced to protect against emergent threats.
While this may sound counterintuitive (i.e., "why would a cybersecurity vendor expose its code?"), the longstanding position of security vendors to close off their code from the community is an act which itself exposes these security firms to become targets for hackers. One undetected attack on security software can end up exposing thousands of customers to vulnerabilities and intrusions, making untold quantities of sensitive data available to malicious actors. Whether attackers are after financial information, trade secrets, blackmail material, or diplomatic scandals, breaking open one black box means attackers can gain the keys to the kingdom.
At Elastic, we believe the best kind of cybersecurity is open. This is best illustrated with Elastic Security Labs, our in-house security research group. Whether it's publishing in-depth research, exposing the most recent cyber threats, or encouraging our community to test our detection rules, Elastic Security is dedicated to making our SIEM solution the best. How do we do this? Partnership and collaboration with our customers, community, and beyond.
Experience the power of SIEM with Elastic Security
Elastic Security is the SIEM solution of choice for leading organizations worldwide. The solution empowers security teams to establish a holistic view of all the data in their ecosystem and — most importantly — act upon that data at the speed and scale required of the modern enterprise.
Elastic Security also seamlessly integrates with other security use cases, including:
Frequently asked questions (FAQs) about SIEM
What is a SIEM?
SIEM stands for security information and event management. These solutions collect logs and events for security teams to analyze.
Why do organizations use SIEM solutions?
Organizations use SIEMs to gather security data from across their systems. This helps them detect suspicious activity early and react quickly. It also simplifies meeting compliance and improves security visibility.
What is the difference between SIEM and SOC?
A security operations center (SOC) is the team responsible for monitoring, analyzing, and investigating security events. A SIEM is the technology utilized by a SOC.
What is AI-driven SIEM?
AI-driven SIEM refers to a SIEM solution that has AI capabilities woven throughout the user experience that help security practitioners with tasks such as alert summarization, query conversion, custom data source ingestion, workflow suggestions, and more. AI-driven SIEM doesn't replace the need for security analysts — rather, it augments their workflows and empowers them to tackle threats more quickly and efficiently.
Can a SIEM help detect ransomware or insider threats?
A SIEM won't block ransomware or insider threats on its own, but it can catch the signs early. It watches for weird patterns or unusual behavior that might indicate an attack. That way, security teams get a heads-up before things spiral out of control.
Is SIEM a firewall?
No, a SIEM is not a firewall. Firewalls are used to control network traffic, while SIEMs aggregate and analyze security data.
What is the difference between SIEM and SOAR?
SIEM specializes in detection of threats, while security orchestration, automation, and response (SOAR) specializes in the organization's broader response to those threats.
What is the difference between SIEM and XDR?
Extended detection and response (XDR) is a solution that investigates and remediates attacks across endpoints specifically, while SIEM works across the entire enterprise. Many SIEM platforms have XDR capabilities built in or integrate with them.
Additional SIEM resources
- 2025 SIEM buyer's guide
- Elastic Global Threat Report
- Explore Elastic Security Labs
- Training: Elastic Security for SIEM
- Discover Elastic AI Assistant for enhanced observability and security
- Is it time to replace your SIEM?
- Tracing history: The generative AI revolution in SIEM
- Security operations center comprehensive guide
- Security analytics comprehensive guide